Difference Between Spear Phishing vs Phishing

What is phishing?
First, the spelling is weird. The term "phishing" came from people who were fans of the "phone phreaks" of the 1960s and 1970s. In the beginning, the phone phreaks used a toy whistle to blow into a phone receiver and make it sound like a Hertz tone.
This tricked the phone company's switching circuit into giving them a free call. This hacking breakthrough led to a new generation of phone phreaks. It took advantage of a flaw in call-routing switches that used in-band communication.
Phishing is like "casting a net" in the digital world. Phishing is when people send emails with a link that leads to a web form on a landing page that looks like a well-known brand, like Microsoft.
The web form asks for personal information, like your username and password. People get phishing emails that say things like "Your account has been closed," "Please change your password," or "Please change your bank account information."
In some cases, the fake web forms look almost like the real thing. But URLs can also show hidden information. You may have to give them your login credentials, social security number, or other personal information in order to get it back from the thieves.
Phishing is also used to get people's Office 365 login credentials. This is also true. To get into Office 365, get shared files, or change your account information, people who aren't supposed to be there will get emails from Office 365.
In the same way as the Bank of America example above, the user clicks on a URL that takes them to a fake Microsoft page.
Spear phishing
Phishing is a way to get your message out to a lot of people. A phishing email is sent to a lot, maybe even a lot, of people at once.
Spear phishing, on the other hand, only tries to get someone to click on a link. They do this by pretending to be you. It does.
A spear phishing attacker has a goal in mind. A cybercriminal posing as a senior employee can ask for wire transfers, direct deposit changes, or W2 information. The attacker may try to act like someone you know, like your coworkers or business acquaintances, to get you to trust them.
The attacker can do this by looking you up on the Internet and social media, or by getting information about you through data breaches that use peer-to-peer (P2P) protocols like BitTorrent.
The CEO of your company is named Joe Smith. You work for him. A spear phisher sees that you're friends with Joe on LinkedIn. He learns about your favourite sports teams and a project you're working on at work from what you write. In the next step, the attacker makes [email protected].
When the real Joe is away, the phisher uses Facebook to find out what he wants to do. The email Joe sent says, "Ugh, Bob." The money I need to send to a Chinese contractor for our project needs to be wired while I'm away. Please solve it right now. Here is a diagram of how the wires are put together.
If you don't pay attention, you could finish the money transfer and lose your money, too. This is a type of email compromise that happens more often than you might think.
Even people who have been trained not to do this get nervous when the "CEO" tells them to do something. Because it's not a stranger.
Phishing vs Spear phishing
- Phishing emails are sent to very large numbers of recipients, more or less at random, with the hope that only a tiny percentage will react.
- Spear phishing emails are meticulously crafted to entice one recipient.
Spare Phishing vs whaling
Whaling uses misleading email communications to target CEOs, CFOs, and other executives. These personnel have access to highly sensitive data such as trade secrets and administrative account passwords.
The attacker sends emails on crucial business matters, posing as a legitimate authority figure. An attacker may, for example, send an email seeking payment to a CEO posing as a client.
In their attacks, whaling attacks always directly address targets by name and phone number, collected from company websites, social media or the press.
Whaling targets only high-ranking individuals within a company, whereas spear phishing normally targets a lower-profile group of individuals.
Barrel phishing vs phishing
The double-barrel approach entails sending two separate emails to a victim to develop trust and legitimacy. But the second email is more sinister.
Email: To make the scenario more realistic, the phisher will delay sending the next email.
Phishing emails are sent to vast numbers of people at random, expecting only a tiny percentage to react. Spear phishing emails are meticulously crafted to garner only one response.
Scam vs. phishing
The main distinction is in targeting. Phishing emails are sent to vast numbers of people at random, expecting only a tiny percentage to react. Spear phishing emails are meticulously crafted to garner only one response.
Spear fishing security
To obtain sensitive information or access to a computer system, phoney communications are sent that look to be genuine. Unwanted information may be downloaded onto a user's computer if a phishing email link is clicked.
Spear phishing examples
An attacker may ask the target to sign a “updated staff handbook.” In this spear phishing email, the attacker poses as HR and urges the target to sign a new employee handbook.
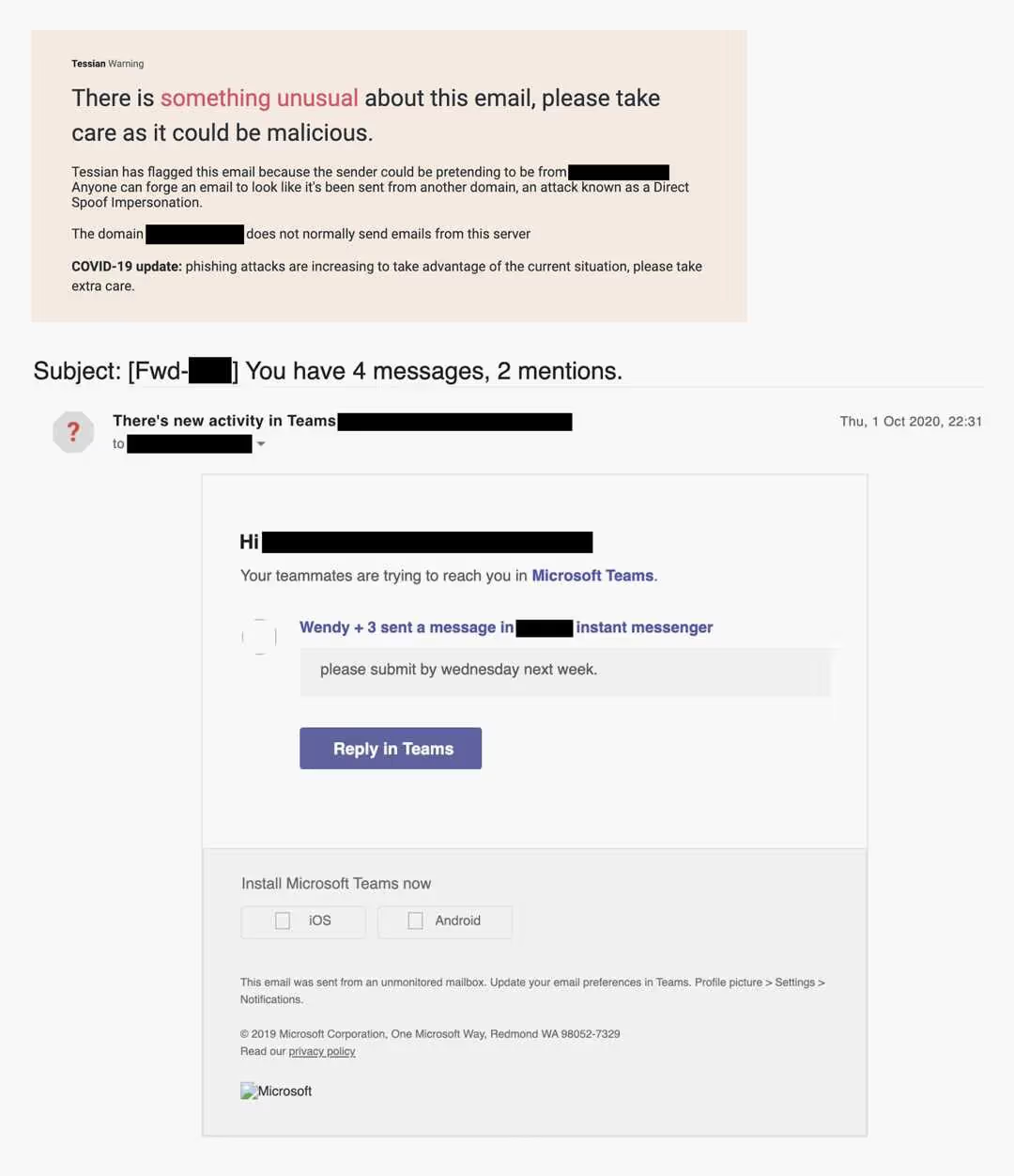
Example 1: A spoof MS Teams notification
Example 2: The assailant poses as a newcomer

Spot phishing
How to Spot Spear Phishing
1. Verify Email Sender
The most common type of spear phishing attack is when someone impersonates someone else. So, one of the most common ways to do this in spear phishing is to make a website with a domain name that looks like a well-known company.
Letters can be used to fool people who aren’t paying attention. Websites are almost completely the same as the real site.
2. Look at the Subject
One of the best ways to tell if someone is trying to do something like this is to look at the subject line. Almost all of these subject lines will try to get you to click on them by making you feel rushed, familiar, or urgent.
The report shows that the five subjects that people use the most are:
- Request a meeting with me (36 percent )
- Following up (14 percent )
- An important thing that needs to be done right away (12 percent )
- Are you free? (10 percent )
- The payment status (5 percent )
3. Files and Links
Many attachments in spear phishing emails have malware in them, or they have forms where you need to enter your most important information. It usually comes in the form of a file called “.exe,” or “exe.” In addition to zip files, PDFs and Word documents are some of the most common types of files that people use.
Take a look at who the email came from to check the attachment’s safety. To do this, hover your mouse over the “from” address.
One of the most recent ways that hackers try to get around security and protection software is to use images instead of text instead.
4. The Message Body
Most of the time, spear phishing emails are made up of your personal information that was found online, like your contact addresses or phone numbers and the names of your pets.
This information is usually not something you would think could be found on the internet.
These targeted emails are very clever, and attackers often choose to play the long game. They try to build a relationship with their victim and gain their trust.
Why is spear phishing so effective
They’re getting better and better, and so are the different ways they come in. Many people around the world are at risk every single day (well, every 30 seconds to be exact). Cyber criminals are getting better at their jobs, and so are their methods.
Your users don’t know about security
The biggest door for cyber criminals to get into is the one marked “security awareness,” and it’s not even close. Most of all, there was not enough training for employees about things like phishing and ransomware.
According to Osterman, only 6% of people have never been taught about security. This is very bad news for an employee’s confidence and ability to recognize and respond to phishing attacks and do the right thing.
Users should be taught to be wary of any unexpected emails or scams that they might come across on different websites and apps.
The money leads the criminals to the people who do bad things
The value of stolen data has dropped because of the Dark Web’s popularity and the fact that people use it. Because information-holders are so good at what they do, they’re now looking there.
Viruses like ransomware, where people are afraid they’ll lose their data, mean that victims don’t have to think twice about agreeing to the demands of the criminal.
There is too little research you do, and you need to spend more time on it
Companies aren’t doing enough to cut down on the risks of phishing and malicious software. There aren’t enough backup procedures in place, and it’s hard to figure out which users need more help.
Also, strong internal control procedures aren’t always in place, like a double check for any bank transfer request that needs to be made (which can be key to preventing CEO fraud). Neglecting these steps puts some of the most common scams right in their crosshairs.




